Ransomware attacks continue to evolve and diversify in tactics. As one part of your security and business continuity strategy, backup planning is critical as a proactive preparation in case your system is attacked.
One day, you see a message of threat, your device is locked, and your data is encrypted. You are under ransomware attack. Although measures have been called for over many years, the number of threat of ransomware attacks is still evident around the world, continuing to disrupt businesses for organizations regardless of size or industry. It is predicted that the damage of ransomware attacks is to exceed $30 billion globally by 20231.
Based on the recent history of ransomware attacks, this article discusses backup as one of the critical components of countermeasures that can be implemented relatively quickly. We will explain why recovery may fail even for systems taking backups and introduce key points to reduce the risk of recovery failure.
What is Ransomware?
Ransomware is a malicious program that locks an infected device or encrypts critical data so that they are unusable, and then demands a ransom in exchange for their recovery.
In recent years, human-operated ransomware attacks (as opposed to automated ransomware attacks) have become mainstream, with human attackers first using vulnerabilities in VPN devices and remote desktops to infiltrate corporate networks. Alternatively, they can enter by sending phishing emails and infecting the device with malware. After breaking into the system, they obtain various permissions to deploy the ransomware, encrypt the files, and send out threatening messages to demand a ransom to be paid for the unlock key.
Ransomware trends
In recent years, there has been an increase in the number of attacks (called "double extortion") where not only is your data encrypted, but is also taken to external servers to publish, if the ransom is not paid.
Ransomware encrypts shared files and data on other servers connected to the network, rendering most of the organization's data useless and potentially shutting down operations.
In addition, there have been reports of cases of infection spreading not only within a single company but also through the supply chain to subsidiaries and business partners ("supply chain attacks”). Organizations with smaller ICT teams and budget are often forced to lower the priority of investing in security, have no security department nor organizational implementation of security policies, and lack internal education and training. These factors result in the likeliness to have vulnerabilities in their systems that make it easier for attackers to gain entry. This means that the attackers may choose to target organizations with these traits, and use it as a springboard to exploit business relationships and attack subsidiaries and business partners.
As with any type of a cyber attack, recovery takes time, money, and effort. In addition, the damage could result in lost opportunities, and the negative impact could also affect business partners.
Proactive preparation - plan your backup
Many government agencies including the FBI2 articulate the importance of firmly implementing the basics of information security measures. Among them, backups are especially important in the event of an infection, as there have been instances where organizations have been able to recover business from or minimize the severity of a ransomware attack3.
Even if ransomware encrypts your data, you may be able to recover your backup data if it’s not infected. For example, at a minimum, keeping backups of the master customer database in the cloud or backing them up to an external storage medium and taking them offline may allow business continuity or reduce recovery time while other data is restored.
However, it is important to note that your backup plan should be created with consideration to reducing failure in restoration. Victims report cases where they have not been able to restore their data from their backups, despite having taken them. One of the major causes for this is when the backup data have also been infected and encrypted by ransomware. Another cause for the failure of restoration is due to old or missing data.
To reduce the risk of recovery failure
When you design a backup operation, you must set the date, time, and interval of the backup appropriately for the point in time you want to return the data to (RPO: recovery point objective). Failure to do so can result in recovery failures due to missing data. Also, multiple generations of backups increase the likelihood of having access to a pre-infection generation. When only the latest generation is backed up, it cannot be used for recovery if this backup was taken without being aware of the infection.
For cases where recovery fails because the data at the backup destination gets encrypted, a more secure destination should be selected to decrease the risk.
Reference
For the "double extortion" attacks mentioned above, it is important to be prepared by encrypting your data so that even if data is stolen, information is not leaked. The decryption key should be stored in a separate location from the data, to reduce the risk of an attacker stealing it .
To make backup destinations more secure
In an intrusive ransomware attack, an attacker targets the backup destination in order to prevent recovery from the backup and more reliably collect the ransom. If you store your backups on disk space or in a shared folder that can be accessed directly by the compromised server, ransomware will also infect and encrypt them, making it impossible to recover your data.
To prevent such damage, the concept of the "3 -2 -1" rule is helpful. This idea of backup to protect critical data from loss and corruption was first proposed in 2012 by US-CERT (United States Computer Emergency Readiness Team), an information security response organization under the US Department of Homeland Security. It is recommended that you store backups according to three rules: keep three copies of files, store them on two different types of media, and store one offsite (for example, physically separate from your facility).
3-2-1 rule
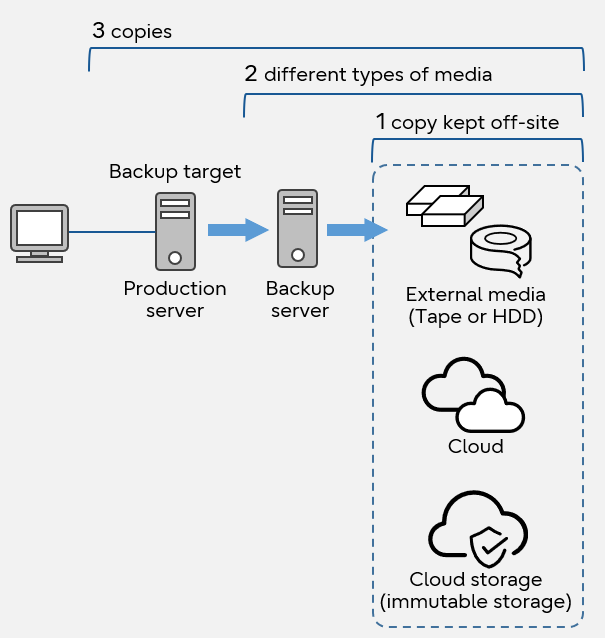
For offsite storage, a backup to an external hard drive or tape which is kept offline (physically isolated) is a powerful cybersecurity solution.
Reference
When a backup is performed online and then separated from the network and stored offline, it is called an "air gap backup." There are various techniques for air gaps, such as using software to logically restrict access to data.
It is also more secure to store it in cloud immutable storage. Immutable storage cannot be rewritten once written. This helps prevent data modification in the event of a ransomware attack. This feature is provided in Azure Blob storage in Microsoft Azure Storage and object locking in Amazon S3 (Simple Storage Service).
Each item is different in terms of ease of handling, cost, and other factors, so consider the requirements such as the type of data you want to store, frequency of backup, and amount of data.
Conduct training
Attacks occur unexpectedly. It is important to make a recovery plan, prepare a manual, and conduct regular training for recovery work so that you can respond quickly in an emergency. Even if you create the manual once, it will become obsolete as the system configuration or operation changes. The recovery plan and manuals should be reviewed and updated regularly. During the training, make sure that you are able to conduct the work properly according to the plan and that you are meeting your recovery point objective (RPO) and recovery time objective (RTO).
Summary
Storing backups in a secure manner improves business continuity, which means better system quality. When considering your IT system strategy, it is important to consider the balance between the level of security and your budget. On the one hand, backup solutions with dedicated storages and communication protocols that can be automated to reduce operational effort can be more secure. But it often incurs more cost. On the other hand, if you don't invest to take measures against security breaches, the risk increases.
Note that the operator capabilities of Fujitsu’s database solution, Fujitsu Enterprise Postgres, controls and manages automatic database backup to object storages. Supported object storages include Amazon S3, Azure Blob Storage, and Google Cloud Storage. For information about Fujitsu Enterprise Postgres operator features and functionality, refer to this page to learn more.
Fujitsu Enterprise Postgres also provides transparent data encryption to encrypt data stored in the database, allowing you to use a cloud key management system as your keystore. This allows you to store encrypted database data and their encryption keys separately.
Sources used in this article
1: https://www.forbes.com/sites/forbestechcouncil/2022/10/31/why-understanding-ransomwares-root-causes-can-help-protect-against-the-evolving-threats/
2: https://www.ic3.gov/Media/PDF/AnnualReport/2022_IC3Report.pdf
3: https://www.cyber.gov.au/threats/types-threats/ransomware








